Data Breach Today, Your Problem Tomorrow: Why Victims Deserve More Than Apologies
TL;DR – Why We Need a Digital FSCS for Breach Victims
In 2025, data breaches are relentless, and when your identity is stolen because a company failed to secure your data, you’re left to pick up the pieces alone. You may be locked out of services, rejected for credit, or forced to prove who you are all over again… while the company responsible recovers, pays a fine to the Treasury, and carries on.
This piece argues for the creation of a Digital Breach Restitution Framework, a kind of digital FSCS, to support breach victims in the UK with:
- ✅ Free credit monitoring and recovery help
- ✅ Breach levies that fund victim support
- ✅ Mandatory transparency and accountability
- ✅ Fast-track support for those locked out of digital services
- ✅ Reform of outdated ID practices (e.g. DOBs, mother’s maiden name)
Current remedies are flawed: Credit monitoring is upsold, CIFAS flags punish victims, and regulatory fines don’t help the people harmed.
📉 The cost to individuals, lost access, stress, financial friction, is invisible in most breach reports.
🔐 Legacy identity systems are still in place, despite better alternatives.
⚖️ Legal rights exist, but are inaccessible to most victims.
We don’t need more apologies or vague advice to “be vigilant.”
We need systems that restore, support, and protect.
👉 What you can do:
- Share your breach story to raise awareness
- Ask your MP to back a Digital Breach Restitution Bill
- Push for reforms to how companies collect, store, and protect PII
📎 Bonus reading: https://muckypaws.com/2025/04/23/data-fines-arent-justice-theyre-just-high-stakes-monopoly-money/
Prefer To Listen?
1. Introduction – When the Breach is Yours
In 2025, data breaches are no longer rare. They’re relentless. Expected. And far too often, they’re swept under the rug until disclosure becomes unavoidable.
When my personal details were compromised via a third-party breach, it took me over 18 months to regain access to my own Government Gateway account. I was locked out of vital public services, including HMRC and Small Claims Court online access. I couldn’t view official correspondence. I couldn’t verify my identity using digital services, despite not having moved house or changed anything in over a decade.
The company responsible for the breach? They carried on.
Me? I was left dealing with the fallout, alone.
When organisations lose your data, you pay the price. It’s time for a restitution system that protects the people, not just the paperwork.
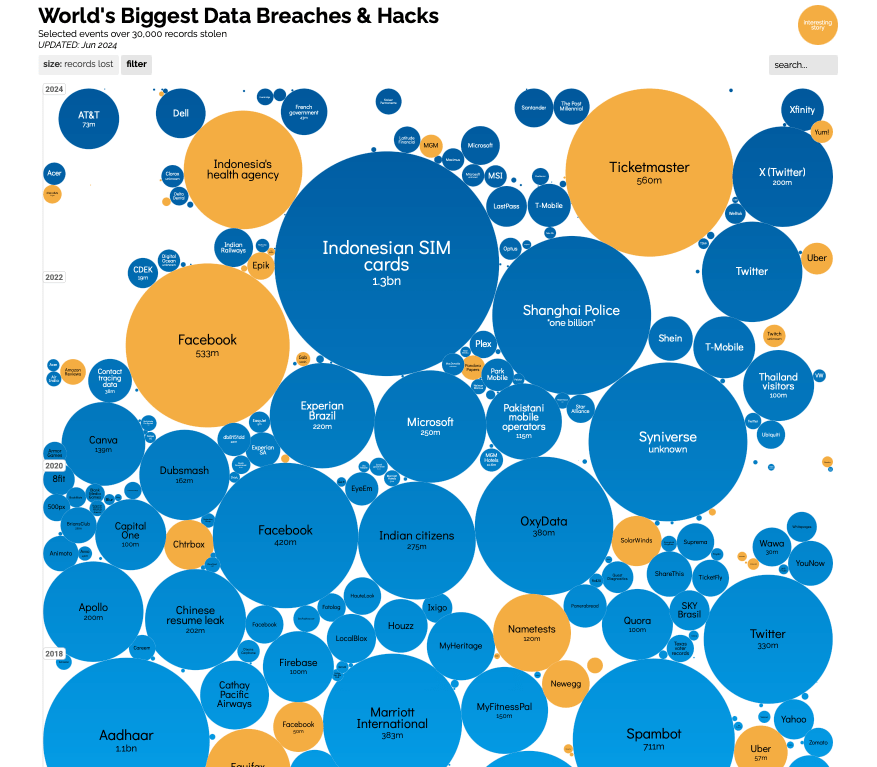
To understand the scale of what’s happening, take a look at this visualisation:
🖼️ https://informationisbeautiful.net/visualizations/worlds-biggest-data-breaches-hacks/
A living infographic showing how billions of records have been lost across healthcare, finance, telecoms, and beyond.
And that’s not even updated for the full extent of 2025.
For every bubble on that chart is a ripple of consequences.
The news moves on. Companies recover.
But the people affected? We’re left to monitor, mitigate, and live with the looming uncertainty of what might come next, without support, without restitution, and without a system designed to catch us when the breach is theirs, not ours.
2. When the Headlines Fade
When a major data breach breaks, the timeline is familiar:
- A brief statement citing “unusual activity”
- A follow-up confirming a breach occurred
- A media frenzy, especially if the name is big enough
- An investigation by the Information Commissioner’s Office (ICO) or another regulator
- A fine. A reprimand.
- Silence.
By then, the company is already moving on. If they’re big enough, they’ll survive the reputational dip. Share prices rebound. PR teams reset.
But the victims?
They’re left with nothing but vague guidance:
- “Monitor your credit report.”
- “Stay alert.”
- “Be vigilant.”
It’s theatre. There’s no direct support. No risk offset. No safety net.
And even if the ICO issues a fine, that money doesn’t go to victims.
It goes to the Treasury, not toward restitution, not toward support, and certainly not toward repairing the damage individuals now face alone.
The real cost of a breach isn’t in the headlines, it’s in the months and years of uncertainty the victims silently endure.
Sometimes, if the breach is particularly egregious, we might even see a public inquiry. But even those rarely focus on the individual experience. They’re audits. Risk reviews. Strategy resets. Not justice.
The current model ensures that organisations can recover, while individuals remain exposed.
🆕 Update July 2025: The Co-op Group just confirmed that all 6.5 million of their members had personal data stolen in a cyber attack, part of a coordinated campaign that hit multiple UK retailers earlier in the year.
The breach wasn’t fully disclosed until months later. And the public FAQs? Offer no specific support beyond generic reassurances.
Once again, the burden is on the individuals to remain vigilant… indefinitely.
🔗 https://www.coop.co.uk/cyber-incident-faqs
🔗 https://www.theguardian.com/business/2025/jul/16/co-op-boss-admits-all-65m-members-had-data-stolen-in-cyber-attack
3. The Cost No One Measures
And the data backs it up.
According to the 2024 IBM–Ponemon Cost of a Data Breach Report, the average cost of a breach to a company is now $4.88 million, with spikes in post-breach response costs and business disruption. Companies pay to restore operations, manage PR fallout, and sometimes issue credit monitoring as a checkbox gesture.
But what’s missing?
Any accounting for the cost to the people whose data was exposed.
No dollar figure for the time spent regaining access to locked accounts.
No metric for the anxiety of knowing your ID might be used tomorrow, or next year.
No estimate for the impact on job searches, credit checks, insurance, or safety.
The report treats victims as entries in a database, not as real people living with real, unpredictable consequences.
Until we recognise that, and legislate accordingly, the system will continue to protect balance sheets, not people.
4. Corporate Apathy – When Basic Security Fails
It’s 2025. MFA is standard. Password managers are free. Security best practices are well-documented and widely adopted.
And yet…
Earlier this year, McDonald’s made headlines, not for a new menu item, but for exposing job applicant data through their McHire chatbot. https://www.malwarebytes.com/blog/news/2025/07/mcdonalds-ai-bot-spills-data-on-job-applicants
A breach enabled by a painfully predictable combination:
- ✅ Default admin credentials
- ❌ No multi-factor authentication
- ❌ No geofencing or IP restrictions
- ❌ No monitoring for suspicious access attempts
This wasn’t a startup under pressure. This was a global brand with ample resources, high public trust, and decades of experience. And they still failed to secure a system responsible for collecting names, emails, phone numbers, addresses, and employment history from thousands of people, many of them applying for minimum-wage roles.
The breach was entirely preventable. The failure wasn’t technical, it was cultural.
Security professionals are often brought in. Advice is given. Controls are proposed.
But all too often, the business decides which risks to accept, to prioritise go-live over governance, speed over security.
The reality is, many organisations are maturing. DevSecOps is gaining traction.
But incidents like McHire show that basic hygiene is still being overlooked, even at the top.
And this isn’t new.
Businesses have operated online since the mid-to-late 1990s. That’s over 30 years of opportunity to learn from past mistakes. But still, we see security training as a tick-box exercise and human fallibility as an unsolved variable.
At security conferences like Black Hat, social engineering competitions continue to reveal just how easily trained professionals can be manipulated. A common tactic? Background audio of a crying baby, to trigger urgency, stress, and empathy from a call handler.
Because here’s the truth: it’s still easier to hack a person than a firewall.
And despite the parade of breaches, we still ask for a date of birth or mother’s maiden name as identity verification. Credentials that were already exposed in breaches years ago.
We need to stop treating identity like it’s static…
…and stop pretending training alone is enough.
Security teams are engaged. Guidance is offered.
But somewhere between risk registers and release deadlines, critical controls are still skipped.
We all need to work harder to shift security from reactive clean-up to proactive design.
5. Time for a Digital FSCS
If your money is lost when a bank collapses, the Financial Services Compensation Scheme (FSCS) steps in. It protects savers. It offers confidence. It acknowledges risk.
But if your identity is stolen through no fault of your own, leaked by a company with poor cyber hygiene, what support do you get?
A generic apology.
A few vague instructions.
Maybe an offer of free credit monitoring, for 12 months, if you’re lucky.
After that? The burden shifts entirely onto you.
The burden of risk has shifted, from institutions to individuals.
And there’s no safety net when digital identity becomes collateral damage.
It’s time for change.
We need a Digital Breach Restitution Fund, a statutory framework that recognises the long-term harm caused by corporate breaches and provides real-world support to those affected.
What could this look like?
- ✅ Free credit monitoring for all breach victims, funded by the organisations responsible
- ✅ Clear, fast-track recovery paths for victims, including human contact and escalation, not just chatbots
- ✅ Mandatory breach response levies, collected and redistributed via a national support fund
- ✅ Transparency obligations: show us what was leaked, how it happened, and what recovery looks like
- ✅ Independent oversight board to review breach responses and restitution handling, ensuring fair treatment and reducing the burden on victims to fight alone.
And what about the fines the ICO imposes?
Right now, they go straight to the Treasury.
The victims get nothing, not even acknowledgement.
That needs to change too.
📝 For more on why regulatory fines don’t equate to justice, I’ve broken it down in this piece:
🔗 https://muckypaws.com/2025/04/23/data-fines-arent-justice-theyre-just-high-stakes-monopoly-money/
If organisations profit from data, they should also be held accountable when they lose control of it.
Not just in headlines, but in real, enforceable obligations to support the people they put at risk.
Until breach victims receive more than generic advice and a shrug, we don’t have a digital safety net.
We have digital neglect.
6. False Remedies – The Illusion of Protection
When your data is compromised, the first thing you’re often offered isn’t help, it’s a subscription.
Credit monitoring. Identity protection. CIFAS markers.
All useful, but only if you know how to use them, and only if you’re prepared to live with the side effects.
Take CIFAS protective registration.
It’s marketed as a shield against impersonation fraud. In practice, it adds friction to you, the victim. You’ll face more ID checks, longer approval times, and rejection from automated systems that don’t know what a CIFAS flag means.
Want to switch broadband?
Apply for a mortgage?
Even open a savings account?
Suddenly, you’re the anomaly. The person who needs to prove they’re not a threat.
CIFAS doesn’t stop fraud. It just changes who gets trusted by default.
Here’s a real-world example:
When I switched broadband providers, my application was automatically rejected online. There was no follow-up, no additional checks. Just rejection. When I called to ask why, I was told, somewhat sheepishly, that because of my CIFAS flag, they couldn’t approve any service costing more than £35 a month.
Despite having a clean credit history, the presence of that flag put me in a “high risk” bucket. Not because of anything I’d done, but because my data had been exposed by someone else’s failure. The protective marker I paid to register (£25 for two years) became a penalty.
Worse still? I wasn’t even reminded when the flag was about to expire.
This isn’t protection. It’s punishment.
Then there’s the glut of credit monitoring services, a booming industry profiting from fear. Some are funded by the same companies who lost your data. Others are upsold after a breach, with a polite note: “For ongoing protection, consider upgrading to our premium tier.”
Let’s be clear: these tools have value.
But they’re not support. They’re not recovery.
And they’re not free for long.
When victims are expected to pay monthly to feel safe after someone else’s failure, something is broken.
Until remedies are built-in, not bolted on, we’re just layering commercial services over systemic negligence.
7. Systemic Reform – What Needs to Change
The problem isn’t just the breaches, it’s the systems we’ve built around them. Systems that are outdated, inconsistent, and too often designed to benefit the organisations, not the individuals.
Back when social media was still gaining traction, my advice to anyone who’d listen, friends, family, fools alike, was simple: never use your real date of birth online. And definitely don’t display it.
Fast forward to today, and that same social media ecosystem is now being used by many organisations as a form of ID verification. Facebook logins. LinkedIn profiles. Identity-as-a-Service wrappers with a smiley UX, built on top of data that was never meant to be secure in the first place.
And yet, even beyond social media, why do so many companies still collect your date of birth as a mandatory field to check out?
Want to buy jeans? Sign up for a newsletter? Pay with your own card or PayPal? You’re still being asked to share one of your most commonly leaked identifiers, under the guise of eligibility, marketing, or tradition.
If it’s not age-restricted, it shouldn’t need your birthdate.
And if it is age-restricted, there are better ways to verify age than permanently storing static personal information.
Start with identity verification. How are we still using “mother’s maiden name” in 2025? How is a date of birth, freely available on most social media, still considered a secure credential? We need to replace legacy methods with modern, risk-based authentication frameworks.
Recovery processes must also be transformed. Getting locked out of essential services should never feel like a Kafkaesque nightmare. Victims need:
- ✅ Fast-track support channels with trained agents
- ✅ Unified processes across government and industry
- ✅ Clear escalation paths, not chatbot loops
We should explore models like verified digital identities, built around user consent, revocation rights, and better auditability. Not perfect, but better than static credentials that never expire.
And what about the legal side?
Did you know you can take a company to court under GDPR if you’ve suffered distress or loss due to a data breach? Most people don’t. It’s buried on an ICO subpage, and the process is often inaccessible and intimidating.
Even when rights exist, the burden is placed entirely on the individual. You must know the law, prove the damage, and fund the case. All because someone else lost control of your data.
Under Article 82 of the UK GDPR, individuals can seek compensation for both material and non-material damage (like emotional distress). But few people know this right exists, and fewer still can afford to act on it.
Let’s not forget that some threat actors go further than phishing or scanning for open ports. The infamous TK Maxx breach of 2007 involved attackers posing as HVAC engineers, gaining physical access, planting rogue devices, and siphoning customer data for over a year.
So while we must call out negligence, we must also recognise that breaches aren’t always simple. Some are advanced. Persistent. Sophisticated.
We also need to talk about data protection beyond compliance.
Some organisations argue that encrypting all personal data, especially at a field level, creates technical complexity or performance trade-offs. That may be true in legacy systems. But it’s 2025. Solutions exist. Excuses don’t.
Full-disk or transparent database encryption is only effective if the attacker steals the storage. But in most modern breaches, attackers access systems via the front door, through credentials, exploits, or APIs. And once inside, unencrypted PII is theirs to take.
🔍 Legal context update: The recently enacted Data (Use and Access) Act 2025 introduces updated data governance obligations and clarified access rights for UK businesses. But it still stops short of mandating direct restitution for victims, reinforcing why we need a stronger, more victim-focused framework.
So while standards like PCI or ISO set useful minimums, they’re not gold standards. And treating them as such only entrenches a “good enough” mentality, until it isn’t.
But whether it’s a default password or an APT, the public shouldn’t carry the burden alone.
True reform will take more than new tools. It will require new thinking, centred on the rights, needs, and realities of breach victims in a digital-first world.
While the UK still lacks direct restitution, other jurisdictions are moving faster. In the US, several states require mandatory breach notifications and victim services. The EU is also exploring expanded support mechanisms under the Digital Services Act.
8. Call to Action – Raise Awareness and Parliamentary Support
The time for passive awareness is over.
We’re beyond posters in staff kitchens and cookie-cutter training modules. What we need now is legislative will and systemic pressure to protect the public after a breach, not just during one.
Because in the current model:
- You get breached.
- You get locked out of essential services.
- You pay for monitoring services.
- You face credit rejections.
- And you shoulder the burden of proving who you are, again and again.
Meanwhile, the organisation responsible pays a fine… to the Treasury.
And carries on.
This cannot remain the default.
What needs to happen:
- A Digital Breach Restitution Framework, akin to the Financial Services Compensation Scheme (FSCS), funded by organisations that suffer repeated or preventable breaches.
- A formal review of identity verification processes, with strict limits on the long-term storage of static credentials like DOBs or maiden names.
- Stronger incentives for organisations to adopt privacy-by-design and post-breach accountability frameworks, including direct support for affected individuals.
- Mandatory reporting of any breach impacting UK citizens, with heightened scrutiny for those involving sensitive data or repeat offences.
What you can do:
- Raise awareness: Share your experiences. Talk about digital vulnerability.
- Write to your MP: Demand legislation that supports breach victims, not just fines for companies.
- Challenge assumptions: Push back when asked to share outdated or insecure identifiers. Advocate for better.
Where the Money Goes Matters
Critics might ask: Who pays for this proposed “Digital FSCS” restitution fund? But the real question is, why aren’t victims already seeing a share of the money collected in their name?
When firms like Meta and Apple are fined over £1.2 billion, those penalties head straight to the Treasury. Not a penny goes to the individuals whose data was lost, misused, or weaponised. The system we’ve built rewards regulators for size of fine, not impact on people.
Even redirecting just 50% of ICO fines from the last three years could have created a substantial restitution fund, enough for credit monitoring, victim support teams, and fast-track identity remediation services.
This isn’t about new money. It’s about just money.
Have a story to tell?
Whether you’ve been impacted by a data breach yourself, or work within an organisation navigating the fallout, your voice matters. The more we surface these stories, of frustration, of resilience, of hard-earned lessons, the harder they are to ignore.
🗣️ Feel free to share your experience in the comments, or link to your own story. Let’s make this a conversation, not just a campaign.
If this piece has resonated with you, there’s more coming.
📄 Want to take action? Use our template letter to write to your MP about the need for stronger breach victim support. It’s ready to download and customise however you see fit.
🏛️ Public policy starts with public pressure. Whether you’re a breach victim or simply want better protection for your future self, real change starts with speaking up.
Because in 2025, “Be vigilant” isn’t a safety net, it’s a shrug.
We deserve better.
Disclaimer: The views expressed in this piece are my own and do not necessarily reflect those of my employer.